

A FortiGate interface is configured with the following commands: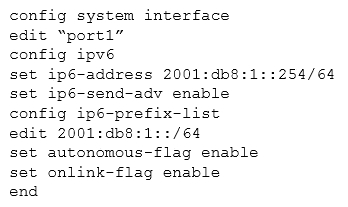
What statements about the configuration are correct? (Choose two.)
Correct Answer:
AC
🗳️
Which of the following Fortinet hardware accelerators can be used to offload flow-based antivirus inspection? (Choose two.)
Correct Answer:
AB
🗳️
Under what circumstance would you enable LEARN as the Action on a firewall policy?
Correct Answer:
C
🗳️
What methods can be used to deliver the token code to a user who is configured to use two-factor authentication? (Choose three.)
Correct Answer:
BCE
🗳️
You are tasked to architect a new IPsec deployment with the following criteria:
- There are two HQ sites that all satellite offices must connect to.
- The satellite offices do not need to communicate directly with other satellite offices.
- No dynamic routing will be used.
- The design should minimize the number of tunnels being configured.
Which topology should be used to satisfy all of the requirements?
Correct Answer:
B
🗳️
View the exhibit.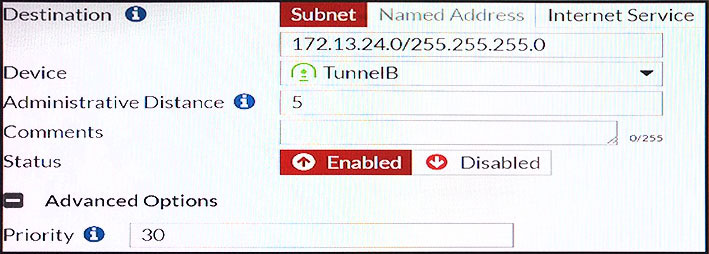
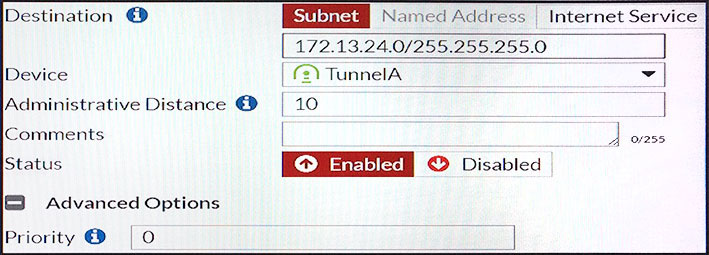
Which of the following statements are correct? (Choose two.)
Correct Answer:
AB
🗳️
Which statements about DNS filter profiles are true? (Choose two.)
Correct Answer:
CD
🗳️
An administrator needs to offload logging to FortiAnalyzer from a FortiGate with an internal hard drive. Which statements are true? (Choose two.)
Correct Answer:
AC
🗳️
Which of the following statements describe WMI polling mode for FSSO collector agent? (Choose two.)
Correct Answer:
BD
🗳️
An administrator observes that the port1 interface cannot be configured with an IP address. What can be the reasons for that? (Choose three.)
Correct Answer:
ABC
🗳️