

DRAG DROP -
Drag and drop the Cisco WSA methods from the left onto the correct deployment modes on the right.
Select and Place:
Correct Answer:
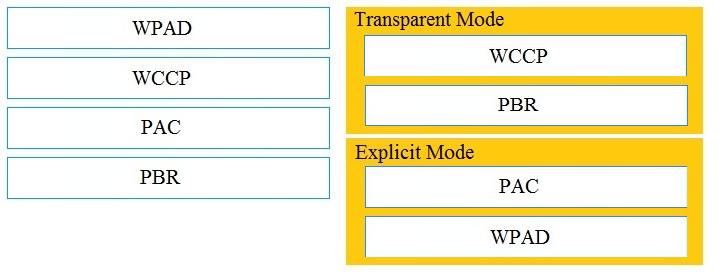
You could use an explicit setting (browser config/PAC/WPAD) or transparent (WCCP/PBR) to point to the first proxy and then the first proxy will route based on category to one of the two upstream proxies based on your policy configuration.
Reference:
https://community.cisco.com/t5/web-security/route-to-wsa-based-on-destination/td-p/2491179
What causes authentication failures on a Cisco WSA when LDAP is used for authentication?
Correct Answer:
B
🗳️
Reference:
https://www.cisco.com/c/en/us/td/docs/security/wsa/wsa11-0/user_guide/b_WSA_UserGuide/b_WSA_UserGuide_appendix_011001.html

Refer to the exhibit. Which statement about the transaction log is true?
Correct Answer:
D
🗳️
Which two features can be used with an upstream and downstream Cisco WSA web proxy to have the upstream WSA identify users by their client IP address?
(Choose two.)
Correct Answer:
AD
🗳️
Reference:
https://www.cisco.com/c/en/us/td/docs/security/wsa/wsa11-0/user_guide/b_WSA_UserGuide/b_WSA_UserGuide_chapter_0100.html