

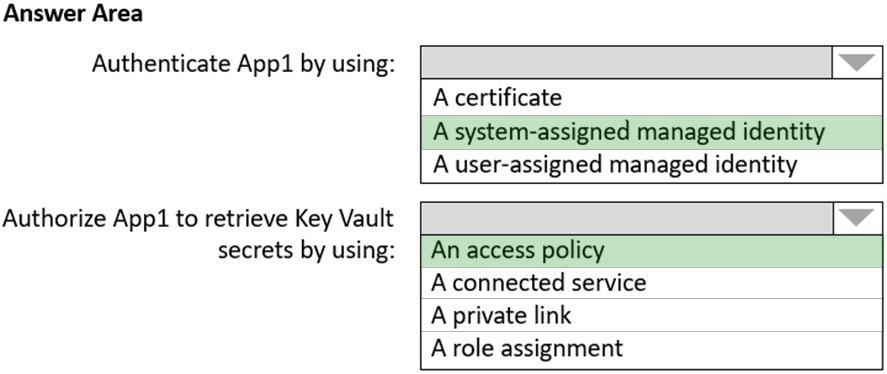
HOTSPOT -
You need to recommend a solution to ensure that App1 can access the third-party credentials and access strings. The solution must meet the security requirements.
What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: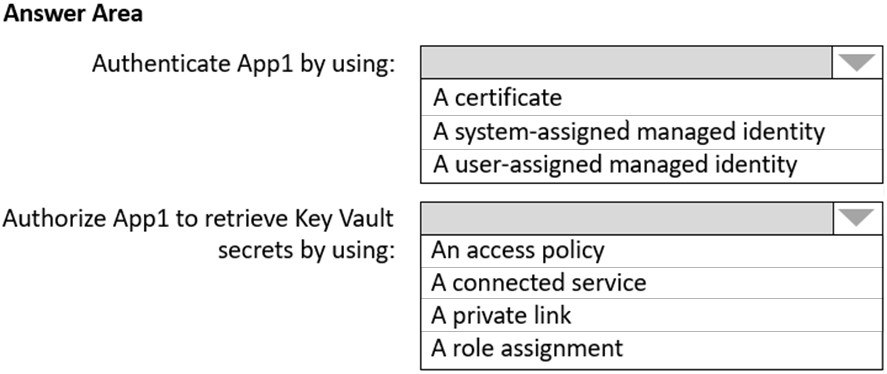
kay000001
Highly Voted 2 years, 7 months agoSnownoodles
2 years, 6 months agoSnownoodles
2 years, 6 months agoAzureJobsTillRetire
2 years, 3 months agoupwork
2 years, 2 months agoAzureJobsTillRetire
2 years, 3 months agoJaQua
Highly Voted 2 years, 6 months agoJay_2pt0
2 years, 5 months agoDeBoer
2 years, 1 month agom1dp
1 year, 8 months agoaharba
Most Recent 4 months ago[Removed]
5 months ago_punky_
5 months, 3 weeks agoSemualulus
7 months agoTeerawee
7 months, 1 week agoubdubdoo
1 year agochair123
1 year, 1 month agochair123
1 year, 1 month agocosmicT73
5 months, 4 weeks agoBShelat
1 year, 4 months agoPaul_white
1 year, 4 months agoStixxNSnares
1 year, 4 months agospotted
1 year, 4 months agopabsinaz
1 year, 6 months agom1dp
1 year, 8 months agostanl2
1 year, 8 months agoNotMeAnyWay
1 year, 9 months ago