

HOTSPOT -
You need to recommend a strategy for securing the litware.com forest. The solution must meet the identity requirements.
What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: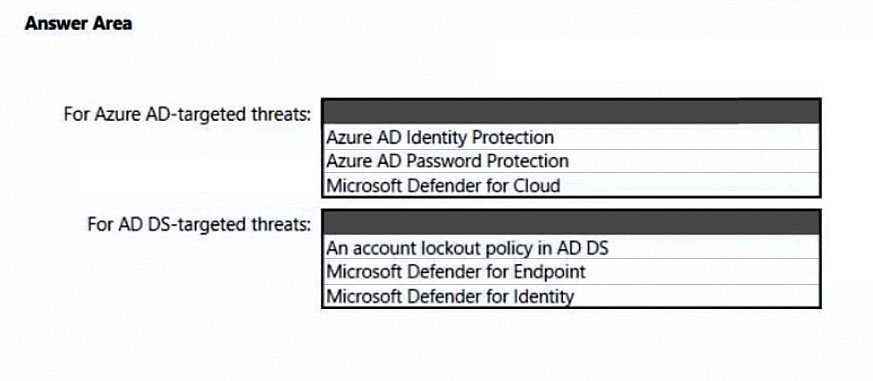

PlumpyTumbler
Highly Voted 2 years, 7 months agoawssecuritynewbie
2 years, 2 months agoBrick69
2 years, 7 months agoJakeCallham
2 years, 6 months agoSam_Gutterson
2 years, 3 months agoJaySapkota
Highly Voted 2 years, 7 months agoBubsator
2 years, 6 months agoJakeCallham
2 years, 6 months agoEr_01
Most Recent 2 months, 3 weeks agojvallespin
8 months, 4 weeks agobesoaus
10 months, 1 week agosubratasen
1 year, 1 month agodsatizabal
3 months agolt9898
1 year, 2 months agoCleggs
1 year, 3 months agoMurtuza
1 year, 3 months agoKdosec
1 year, 4 months agocybrtrk
1 year, 5 months agorishiraval007
1 year, 6 months agoslobav
1 year, 7 months agoCatoFong
1 year, 7 months agozellck
1 year, 11 months agozellck
1 year, 11 months agoKallMeDan
2 years agoKallMeDan
2 years agoGurulee
2 years, 1 month ago