

HOTSPOT -
You have an Azure Active Directory (Azure AD) tenant that contains the users shown in the following table.
You have the locations shown in the following table.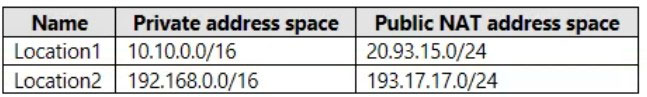
The tenant contains a named location that has the following configurations:
✑ Name: Location1
✑ Mark as trusted location: Enabled
IPv4 range: 10.10.0.0/16 -
MFA has a trusted IP address range of 193.17.17.0/24.
✑ Name: CAPolicy1
✑ Assignments
- Users or workload identities: Group1
- Cloud apps or actions: All cloud apps
✑ Conditions
- Locations: All trusted locations
✑ Access controls
- Grant
- Grant access: Require multi-factor authentication
- Session: 0 controls selected
✑ Enable policy: On
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: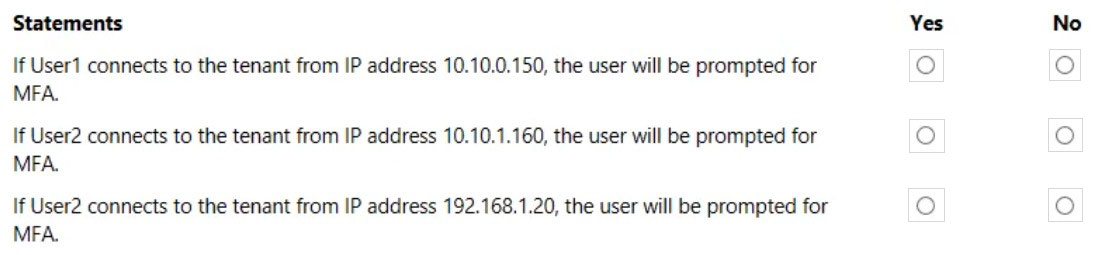

dejo
Highly Voted 2 years, 7 months agof2bf85a
2 years agoNail
6 months, 1 week agoaks_exam
1 year, 2 months agoNail
6 months, 1 week agohyc1983
Highly Voted 2 years, 5 months agoMrPrasox
2 years, 5 months agomibur
2 years, 4 months agowooyourdaddy
2 years, 3 months agokanew
1 year, 11 months agokanew
1 year, 11 months agoNivos23
1 year, 5 months agob233f0a
1 year, 10 months agod1e85d9
Most Recent 1 month, 2 weeks agoanonymousarpanch
2 months, 2 weeks agocsi_2025
2 months agoarmid
2 months, 2 weeks agoRemmyT
10 months, 3 weeks agoRucasII
11 months, 3 weeks agoemartiy
1 year, 1 month agozlzl
1 year, 2 months agoShuihe
1 year, 2 months agoNyamnyam
1 year, 5 months agosyougun200x
1 year, 7 months agoHawklx
1 year, 10 months agoServerBrain
1 year, 7 months agoivzdf
1 year, 9 months agoivzdf
1 year, 9 months agokanew
1 year, 11 months agokanew
1 year, 11 months agoJBail
2 years agokanew
1 year, 11 months agoHolii
1 year, 10 months agoHolii
1 year, 10 months agof2bf85a
2 years agof2bf85a
2 years agoiwantmyexamsobad
2 years ago