

HOTSPOT -
You have the Azure environment shown in the Azure Environment exhibit.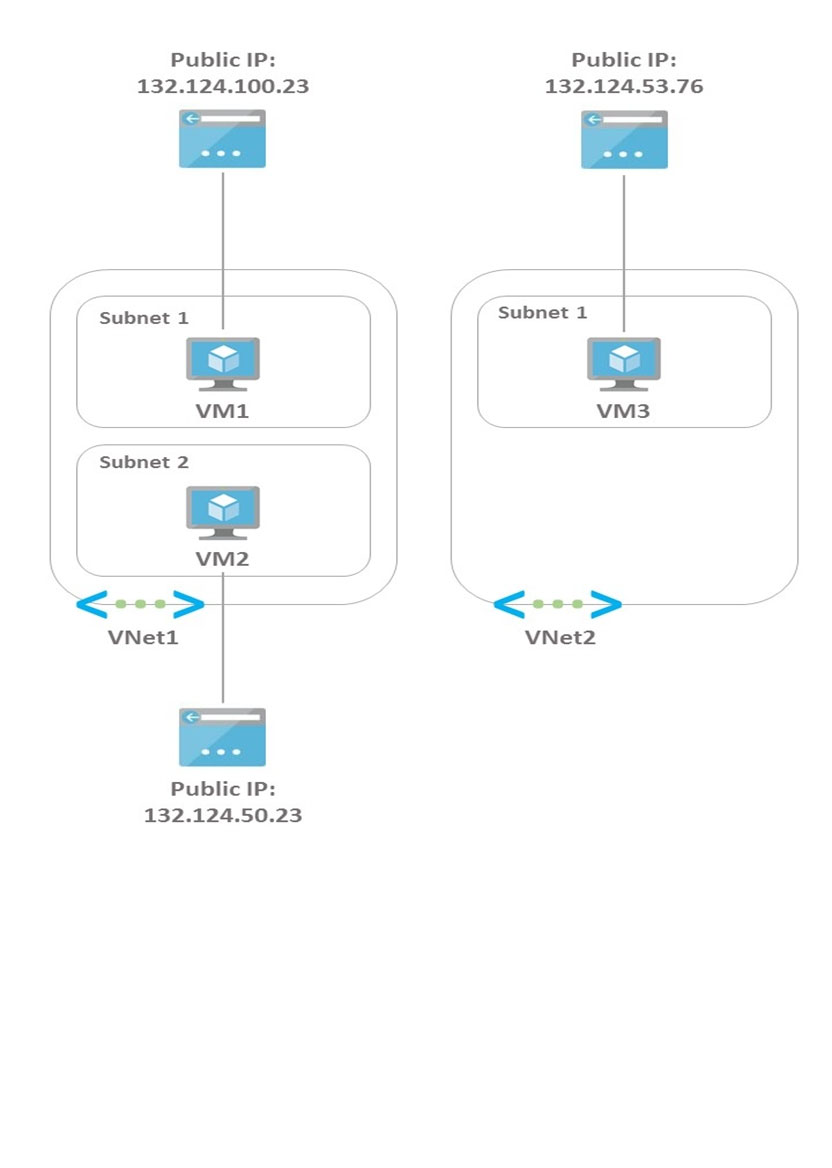
The settings for each subnet are shown in the following table.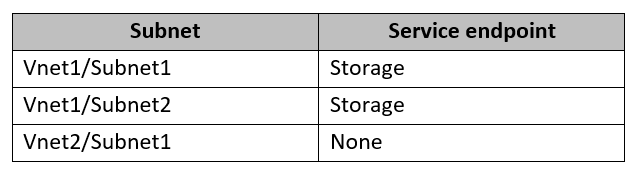
The Firewalls and virtual networks settings for storage1 are configured as shown in the Storage1 exhibit.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: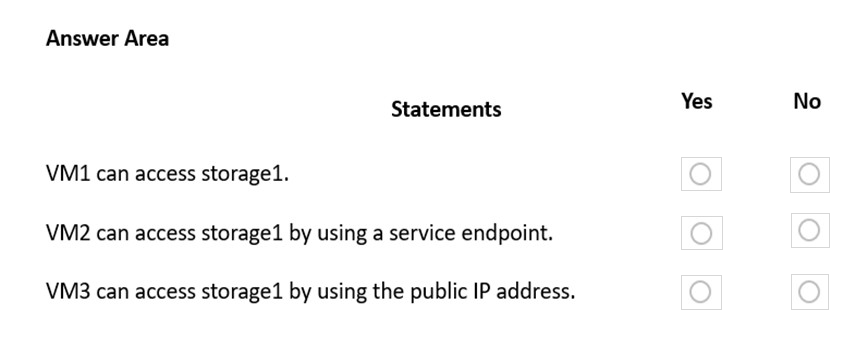
Jamesat
Highly Voted 2 years, 10 months agoGoofer
2 years, 5 months agoflurgen248
2 years, 3 months agoJulienYork
Highly Voted 3 years, 1 month agomanhattan
5 months, 3 weeks agomanhattan
5 months, 1 week ago0dc759b
9 months, 1 week agostormtraining
7 months, 3 weeks agojellybiscuit
2 years, 9 months agosapien45
2 years, 9 months agosapien45
2 years, 8 months agoAjdlfasudfo0
2 years, 7 months agoTakloy
2 years, 6 months agoLazylinux
Most Recent 1 year, 6 months agoLazylinux
1 year, 6 months agoMurad01
1 year, 6 months agoazure_dori
1 year, 10 months agomabalon
1 year, 10 months agoTJ001
2 years, 5 months agochatlisi
2 years, 5 months ago_fvt
2 years, 2 months agounclegrandfather
3 years agopinchocr
3 years agoJun_AZ500
3 years agojpetix
3 years, 1 month agowsrudmen
3 years, 1 month agoPayday123
3 years ago