

HOTSPOT -
You have an Azure subscription that contains the virtual machines shown in the following table.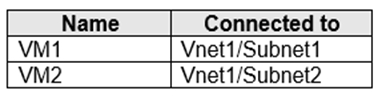
Subnet1 and Subnet2 are associated to a network security group (NSG) named NSG1 that has the following outbound rule:
✑ Priority: 100
✑ Port: Any
✑ Protocol: Any
✑ Source: Any
✑ Destination: Storage
✑ Action: Deny
You create a private endpoint that has the following settings:
✑ Name: Private1
✑ Resource type: Microsoft.Storage/storageAccounts
✑ Resource: storage1
✑ Target sub-resource: blob
✑ Virtual network: Vnet1
✑ Subnet: Subnet1
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: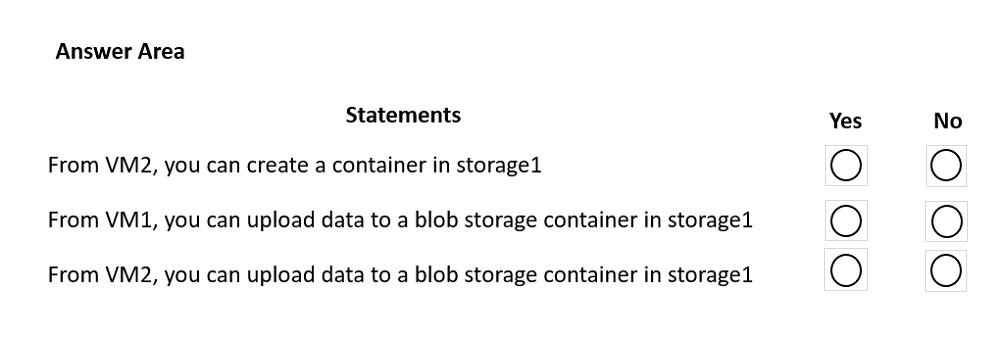
WorkHardBeProud
Highly Voted 3 years, 6 months agoPamban
3 years, 4 months agowaqas
3 years, 4 months agoSergovladi
3 months agoSergovladi
3 months agoleotoronto123
3 years, 3 months agosapien45
2 years, 6 months agoPamban
3 years, 4 months agoTakloy
3 years, 3 months agochristianpageqc
Highly Voted 3 years, 6 months agoRoman_Rabodzey
3 years, 6 months agosrikanth1987
3 years, 5 months agoRandomUser
3 years, 6 months agosapien45
2 years, 6 months agoBharat
3 years, 6 months agoWorkHardBeProud
3 years, 6 months agoAjdlfasudfo0
2 years, 4 months agoMorgana
3 years, 6 months agoxRiot007
Most Recent 2 weeks, 6 days agoSaba53
2 months, 2 weeks agoMostafaNawar
1 year, 3 months agoLazylinux
1 year, 7 months agoLazylinux
1 year, 7 months agoironbornson
1 year, 6 months agoheatfan900
1 year, 7 months agopentium75
8 months, 4 weeks agomabalon
1 year, 7 months agopentium75
8 months, 4 weeks agoCrazysaffer
1 year, 11 months ago25max
2 years ago_fvt
2 years ago_fvt
2 years agoJennyHuang36
2 years, 2 months agotzatziki
2 years, 2 months agoTJ001
2 years, 3 months agophoenix14
2 years, 4 months agoTakloy
2 years, 5 months agodaemon101
1 year, 9 months agoDisparate
2 years, 5 months ago