

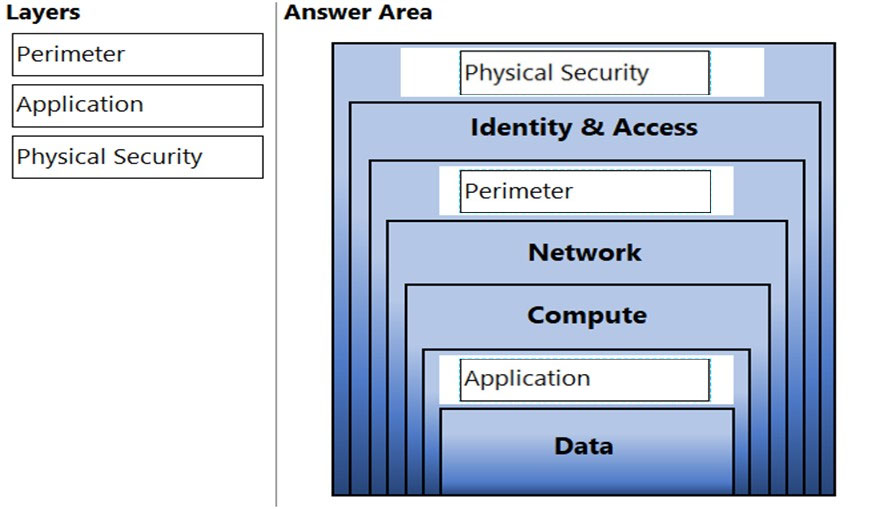
DRAG DROP -
You need to complete the defense-in-depth strategy used in a datacenter.
What should you do? To answer, drag the appropriate layers to the correct positions in the model. Each layer may be used once, more than once, or not at all.
You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place: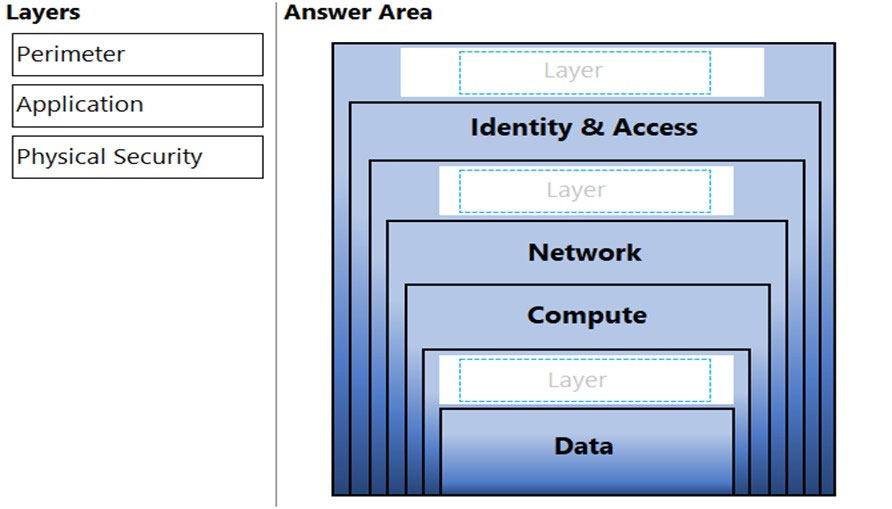
kamal_004
Highly Voted 1 year, 10 months agoAlexKK
Highly Voted 1 year, 5 months agoliya1
Most Recent 3 months, 4 weeks agoSabuniq
5 months ago20142365
1 year, 1 month agoOlikuTR
1 year, 3 months agoaslam8526
1 year, 9 months agonewbie
1 year, 9 months agoSJ_JHA
2 years, 3 months agoKrissy90
2 years, 5 months agoVick98
1 year, 8 months ago[Removed]
2 years, 5 months agousit
2 years, 10 months agoMev4953
2 years, 10 months ago754a
2 years, 11 months agoamine11
2 years, 10 months ago