

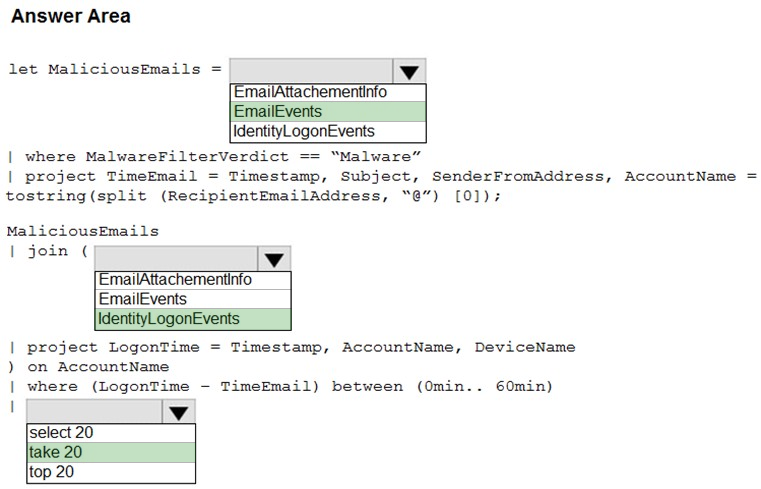
HOTSPOT -
You are informed of an increase in malicious email being received by users.
You need to create an advanced hunting query in Microsoft 365 Defender to identify whether the accounts of the email recipients were compromised. The query must return the most recent 20 sign-ins performed by the recipients within an hour of receiving the known malicious email.
How should you complete the query? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: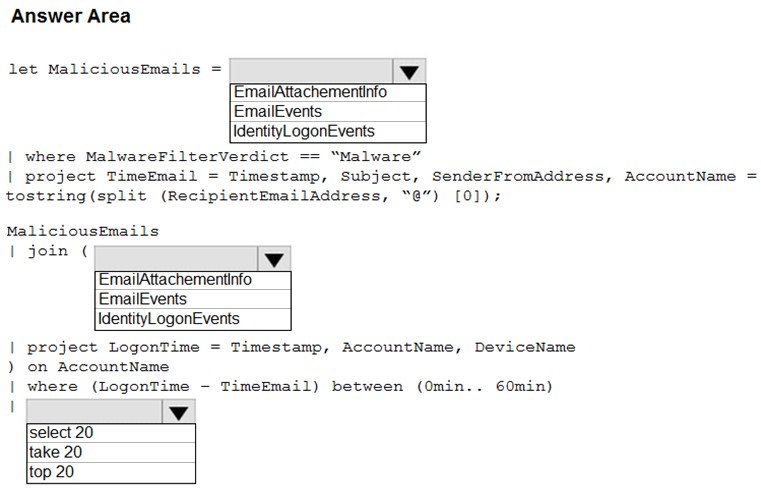
pedromonteirozikado
Highly Voted 3 months agoTuitor01
2 weeks, 1 day agojasonfmj
Highly Voted 2 months, 4 weeks agoThezuland1098
Most Recent 2 months, 2 weeks agotalosDevbot
2 months, 2 weeks agooreoale
2 months, 4 weeks agog_man_rap
4 months agoemartiy
6 months, 2 weeks agochepeerick
1 year, 2 months agotatendazw
1 year, 6 months agoRamkid
1 year, 11 months agodanb67
1 year, 2 months agodanb67
1 year, 2 months agoFukacz
2 years, 3 months agodanb67
1 year, 2 months agoits_me_Nat
2 years, 9 months agojetodo7615
2 years, 11 months agoRandomNickname
2 years, 11 months agoReginaldoBarreto
3 years agopedromonteirozikado
2 years, 10 months agozedricko
3 years agoj888
2 years, 8 months ago