

HOTSPOT -
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table.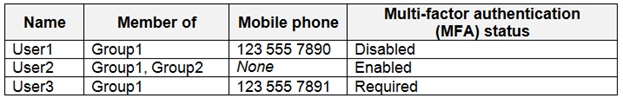
You create and enforce an Azure AD Identity Protection user risk policy that has the following settings:
✑ Assignment: Include Group1, Exclude Group2
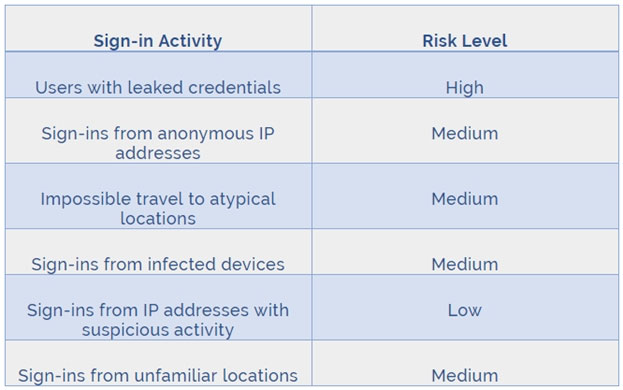
✑ Conditions: Sign-in risk of Medium and above
✑ Access: Allow access, Require password change
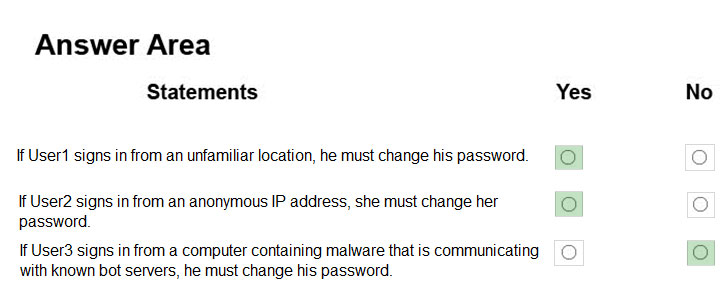
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: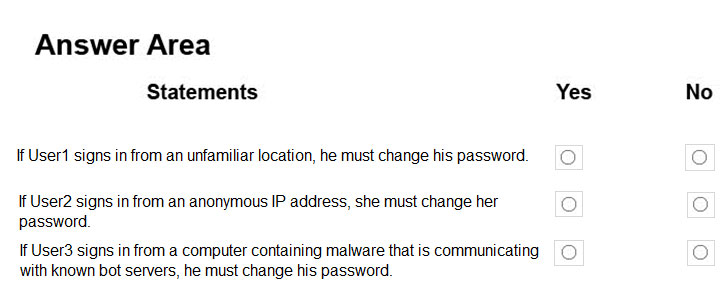
Geeky93
Highly Voted 4 years agokitus
9 months agoITFranz
2 months, 2 weeks agoPatchfox
3 years, 2 months agovtoroynah
3 years, 1 month agorctm_bm
Highly Voted 3 years, 12 months agoVikku30
3 years, 2 months agorgullini
3 years, 11 months agoudmraj
3 years agoJCWF
3 years, 11 months agocannibalcorpse
3 years, 11 months agocfsxtuv33
3 years, 2 months agorctm_bm
3 years, 8 months agoSofiaLorean
Most Recent 4 days, 3 hours agoMarcoHurry
4 months, 1 week agopentium75
7 months, 2 weeks agoShambhuSNair
7 months, 3 weeks agoJkayx94
1 year agoABIYGK
1 year, 3 months agoxRiot007
8 months agowardy1983
1 year, 4 months agojimmyjose
1 year, 3 months agoMeisAdriano
1 year, 5 months agoGaryKing123
1 year, 5 months agoJunetGoyal
1 year, 5 months agofireb
1 year, 5 months agoxRiot007
8 months agoArchitectX
1 year, 6 months agoheatfan900
1 year, 6 months agoP4ndem1c
1 year, 7 months agosommyo
1 year, 7 months agoAzureAdventure
1 year, 7 months ago