

The Development and External teams have the project viewer Identity and Access Management (IAM) role in a folder named Visualization. You want the
Development Team to be able to read data from both Cloud Storage and BigQuery, but the External Team should only be able to read data from BigQuery. What should you do?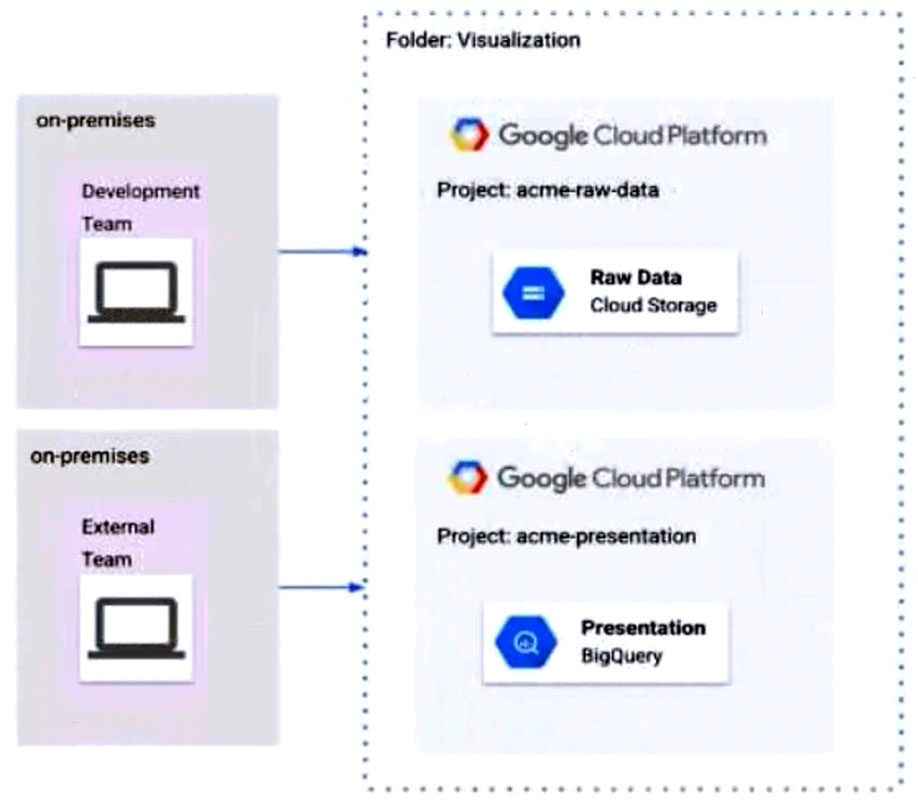
AWSandeep
Highly Voted 2 years, 1 month agoOleksandr0501
1 year, 5 months agoOleksandr0501
1 year, 5 months agoOleksandr0501
1 year, 5 months agoTNT87
2 years, 1 month agomaci_f
Highly Voted 1 year, 9 months agojosech
Most Recent 5 months, 1 week agoAman47
10 months, 2 weeks agoMamko
1 year, 1 month agotechabhi2_0
1 year, 1 month agowan2three
1 year, 2 months ago[Removed]
1 year, 2 months agoizekc
1 year, 5 months agomidgoo
1 year, 7 months ago[Removed]
1 year, 9 months agozellck
1 year, 11 months agoTNT87
1 year, 9 months agoOleksandr0501
1 year, 5 months agoAtnafu
1 year, 11 months agoAtnafu
1 year, 11 months agocloudmon
1 year, 11 months agocloudmon
1 year, 11 months agocloudmon
1 year, 11 months agoyu_
1 year, 11 months agojkhong
1 year, 11 months agojosrojgra
1 year, 12 months agoTNT87
2 years ago