

Your company has a project in Google Cloud with three Virtual Private Clouds (VPCs). There is a Compute Engine instance on each VPC. Network subnets do not overlap and must remain separated. The network configuration is shown below.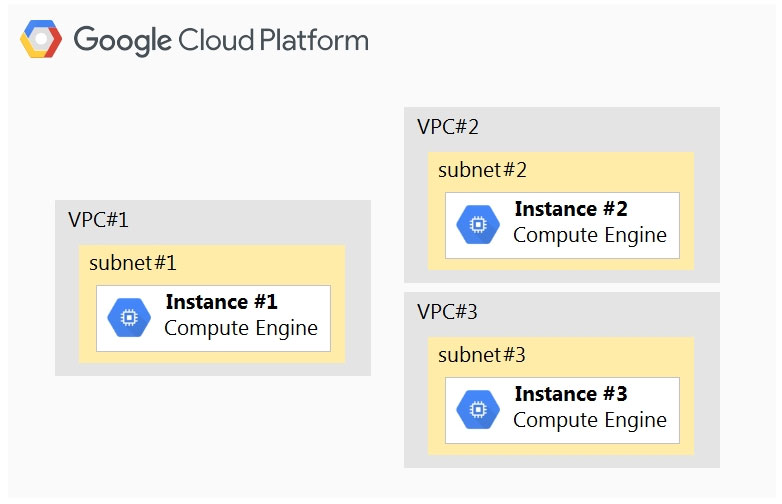
Instance #1 is an exception and must communicate directly with both Instance #2 and Instance #3 via internal IPs. How should you accomplish this?
XDevX
Highly Voted 4 years agolazybeanbag
3 years, 12 months agoIshu_awsguy
2 years, 11 months agob6f53d8
1 year, 9 months agoJeffClarke111
4 years agoIshu_awsguy
2 years, 11 months agoPankaj_007
2 years, 8 months agosameer2803
2 years, 6 months agoMamthaSJ
Highly Voted 4 years agocoutcin
3 years, 2 months agoplumbig11
Most Recent 6 months, 2 weeks agoawsgcparch
11 months, 3 weeks agoafsarkhan
1 year agodija123
1 year, 3 months agoshashii82
1 year, 4 months agokshlgpt
1 year, 6 months agoAdityaGupta
1 year, 9 months agorusll
1 year, 11 months agonatpilot
2 years, 3 months agomifrah
2 years, 3 months agorazabpn
2 years, 5 months agoexamch
2 years, 6 months agothamaster
2 years, 6 months agoANKITMANDLA
2 years, 7 months agoPankaj_007
2 years, 8 months agoPankaj_007
2 years, 8 months ago