

You have deployed an HTTP(s) Load Balancer with the gcloud commands shown below.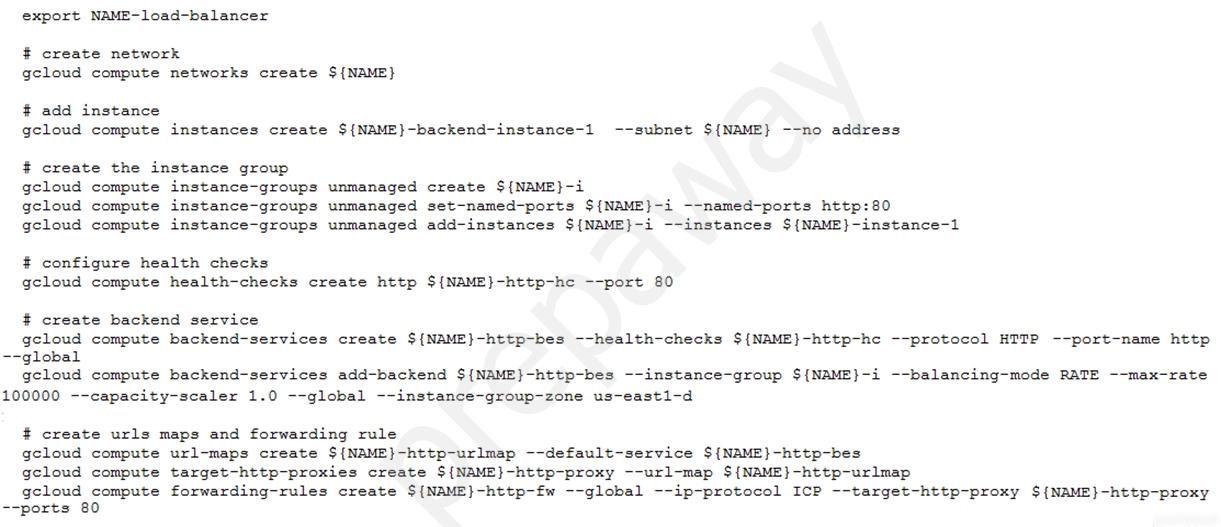
Health checks to port 80 on the Compute Engine virtual machine instance are failing and no traffic is sent to your instances. You want to resolve the problem.
Which commands should you run?
gcper
Highly Voted 3 years, 8 months agosyu31svc
3 years, 4 months agosantoshchauhan
Most Recent 7 months, 3 weeks ago__rajan__
1 year, 1 month agoomermahgoub
1 year, 10 months agotomato123
2 years, 2 months agowilwong
3 years, 3 months agomaleksah
3 years, 9 months agojcataluna
1 year, 11 months agoyuchun
3 years, 4 months agodonchick
3 years, 10 months ago