

You've deployed a microservice called myapp1 to a Google Kubernetes Engine cluster using the YAML file specified below: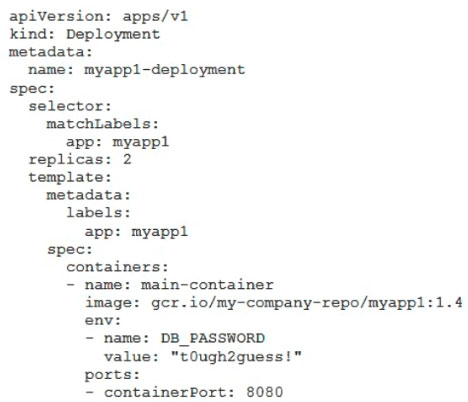
You need to refactor this configuration so that the database password is not stored in plain text. You want to follow Google-recommended practices. What should you do?
rramani7
Highly Voted 4 years, 7 months agosaurabh1805
Highly Voted 4 years, 7 months agohjyhf
3 years, 5 months ago68f26bd
Most Recent 3 months, 3 weeks ago559b96d
7 months agosubha.elumalai
7 months, 1 week agoSandy8
1 year agoMohit__
1 year agogsmasad
1 year, 2 months agobearfromoso
1 year, 3 months agoCaptain1212
1 year, 4 months agobobthebuilder_karkedikhayenge
1 year, 4 months agosthapit
1 year, 4 months agoExamsFR
1 year, 5 months agoraselsys
1 year, 9 months agoPB78
1 year, 10 months agoBuruguduystunstugudunstuy
1 year, 10 months agoDi4sa
1 year, 11 months ago