

A penetration tester has gained access to part of an internal network and wants to exploit on a different network segment. Using Scapy, the tester runs the following command: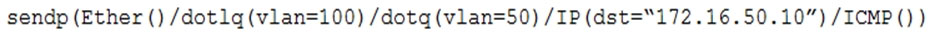
Which of the following represents what the penetration tester is attempting to accomplish?
Incognito09
Highly Voted 2 years, 6 months ago[Removed]
Highly Voted 2 years, 3 months agoEtc_Shadow28000
Most Recent 9 months, 4 weeks agoPhillyCheese
1 year, 4 months agomehewas855
1 year, 4 months ago[Removed]
2 years agonickwen007
2 years, 1 month ago[Removed]
2 years, 1 month agokenechi
2 years, 2 months ago[Removed]
2 years, 2 months ago