

After gaining access to a previous system, a penetration tester runs an Nmap scan against a network with the following results: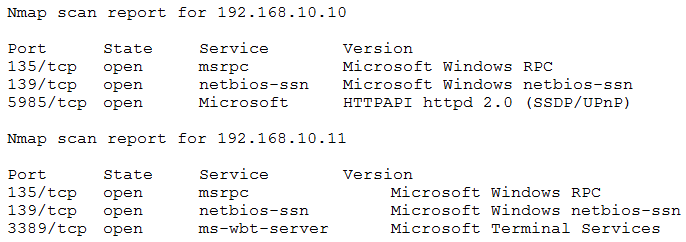
The tester then runs the following command from the previous exploited system, which fails: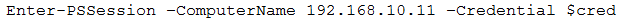
Which of the following explains the reason why the command failed?
Neolot
Highly Voted 2 years, 6 months agoManzer
Highly Voted 2 years, 6 months agoaleXplicitly
2 years, 1 month agozemijan
Most Recent 5 months, 4 weeks agofuzzyguzzy
8 months, 1 week agoCCSXorabove
9 months, 1 week agoEtc_Shadow28000
9 months, 3 weeks agoLiveLaughToasterBath
1 year, 3 months agoKeToopStudy
1 year, 3 months agobieecop
1 year, 8 months agobiggydanny
1 year, 12 months agobiggydanny
1 year, 12 months agoOnA_Mule
2 years ago[Removed]
2 years agocy_analyst
2 years agoAaronS1990
2 years agoBrayden23
2 years, 1 month agoKingIT_ENG
2 years, 1 month agoKingIT_ENG
2 years, 1 month agoKingIT_ENG
2 years, 1 month agonickwen007
2 years, 1 month ago[Removed]
2 years, 1 month ago[Removed]
2 years, 1 month ago