

Security analysts are conducting an investigation of an attack that occurred inside the organization's network. An attacker was able to collect network traffic between workstations throughout the network. The analysts review the following logs: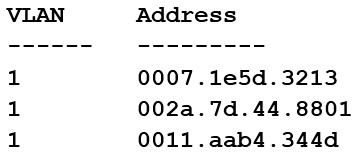
The Layer 2 address table has hundreds of entries similar to the ones above. Which of the following attacks has MOST likely occurred?
rodwave
Highly Voted 2 years, 7 months agoMumbo
Highly Voted 1 year, 7 months agoKheeze1
1 year, 7 months agoPesos
1 year, 4 months agoslackbot
Most Recent 3 months, 3 weeks agoProtract8593
1 year, 11 months agoYawannawanka
2 years, 2 months agofouserd
2 years, 2 months agoRonWonkers
2 years, 9 months ago_Tyler_
2 years, 9 months agoScottT
2 years, 9 months agoYuyuyakuza
2 years, 9 months ago