

SIMULATION -
An attack has occurred against a company.
INSTRUCTIONS -
You have been tasked to do the following:
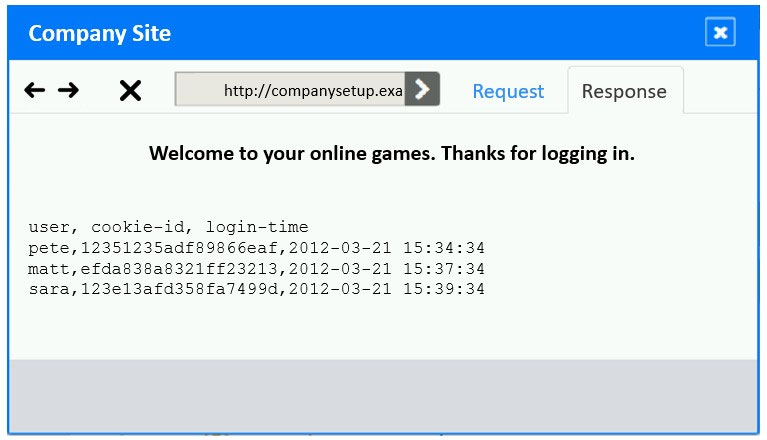
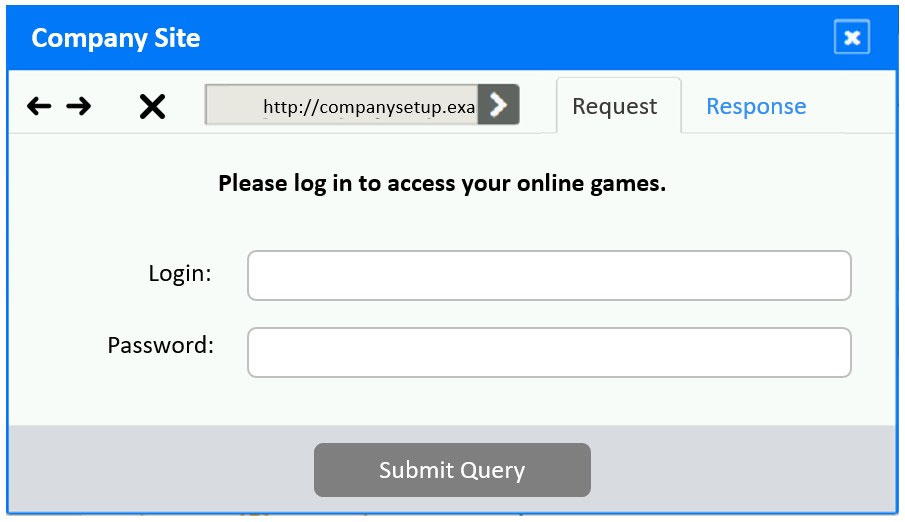
✑ Identify the type of attack that is occurring on the network by clicking on the attacker's tablet and reviewing the output.
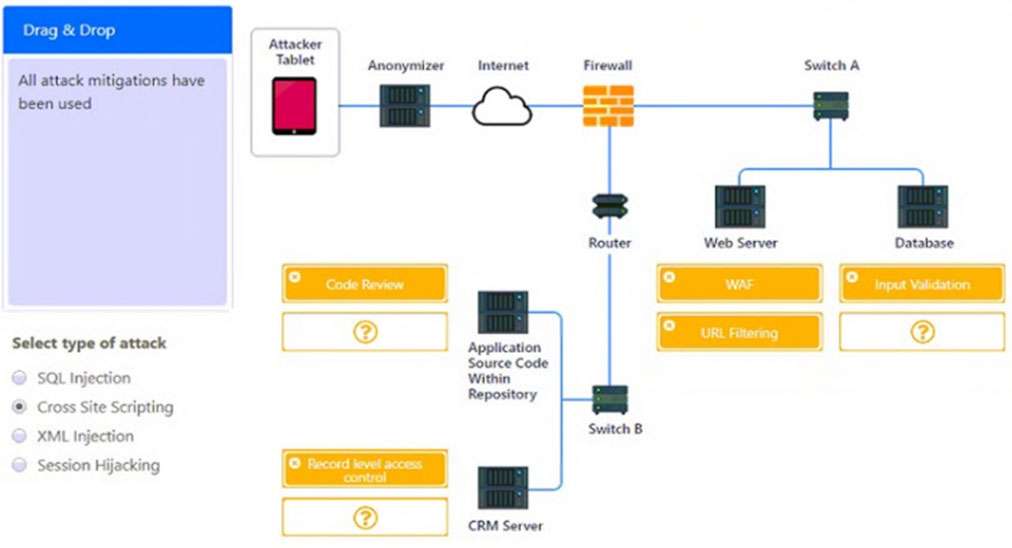
✑ Identify which compensating controls a developer should implement on the assets, in order to reduce the effectiveness of future attacks by dragging them to the correct server.
All objects will be used, but not all placeholders may be filled. Objects may only be used once.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.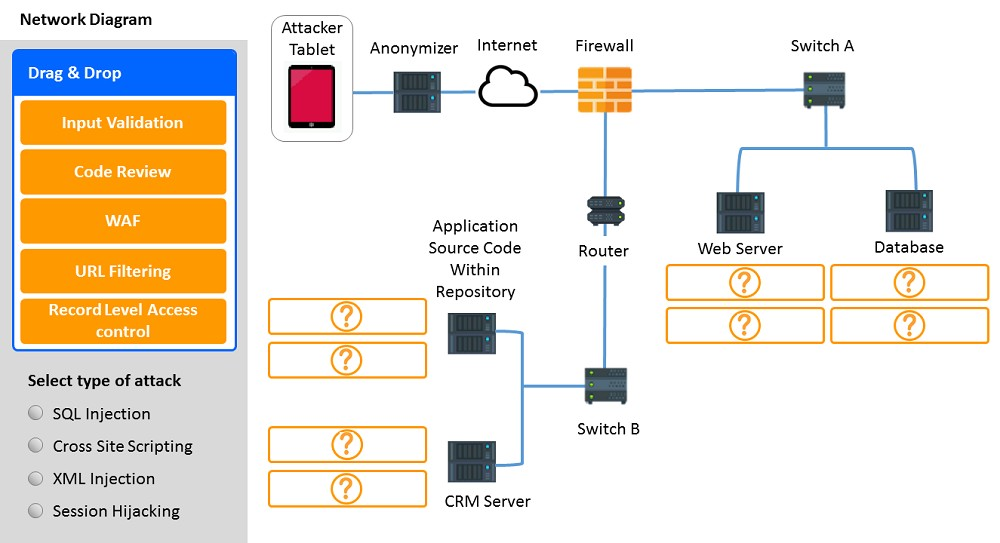

stoneface
Highly Voted 2 years, 7 months agohoneybussy
11 months agoLordJaraxxus
1 year, 1 month agostoneface
2 years, 7 months agoProtract8593
1 year, 8 months agoKnowledge33
2 years, 5 months agoLionel_TheITGuy
2 years, 3 months agoKetReeb
2 years, 7 months agostoneface
2 years, 7 months agoanonimouse2
2 years, 7 months agofryderyk
1 year, 6 months agoOld_Boy_
1 year, 5 months agonobnarb
Highly Voted 2 years, 5 months agoDJCODING
2 years, 1 month agoBD69
1 year agoAbdullahMohammad251
Most Recent 10 months, 1 week agofb8c9bb
9 months, 3 weeks agoGigaChungus
1 year agoreto1
1 year ago7308365
1 year, 2 months agoBD69
1 year ago7308365
1 year, 2 months agoBD69
1 year agoPaula77
1 year, 1 month agoRumchata556
1 year, 4 months agoIlginz
1 year, 4 months agoFrogalicious
1 year, 5 months agoGustavSvenson
1 year, 5 months agoDashRyde
1 year, 6 months agoabove
1 year, 8 months agoDriftandLuna
1 year, 8 months agoMorganB
1 year, 11 months agoMS2023
1 year, 11 months agoAttila777
1 year, 11 months agomosher21
1 year, 12 months agoBD69
1 year agoEduardosSS
2 years agoBYU
2 years, 1 month agoMarito1414
2 years, 1 month ago