

A penetration tester discovered a vulnerability that provides the ability to upload to a path via directory traversal. Some of the files that were discovered through this vulnerability are: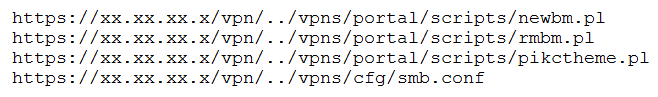
Which of the following is the BEST method to help an attacker gain internal access to the affected machine?
lifehacker0777
2 years ago[Removed]
2 years, 8 months agoTheITStudent
2 years, 9 months ago