

A customer reports being unable to connect to a website at www.test.com to consume services. The customer notices the web application has the following published cipher suite: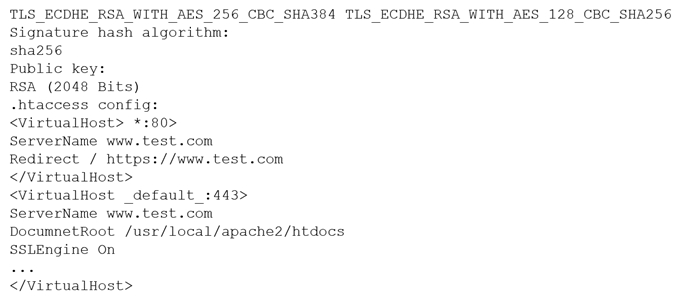
Which of the following is the MOST likely cause of the customer's inability to connect?
snilu
Highly Voted 3 years agoBiteSize
Highly Voted 1 year, 9 months agoBiteSize
1 year, 9 months agoblacksheep6r
Most Recent 2 months, 2 weeks agoblacksheep6r
2 months, 2 weeks agogrelaman
6 months, 1 week agogrelaman
6 months, 1 week ago23169fd
9 months, 2 weeks agoDelab202
1 year, 3 months agollamaPaja
1 year, 9 months agoFOURDUE
2 years, 3 months agoangryelvis
2 years, 4 months agokycugu
2 years, 4 months agolordguck
2 years, 5 months agoAndre876
2 years, 5 months agoSloananne
2 years, 7 months agodangerelchulo
2 years, 7 months agoito4862
2 years, 4 months agoito4862
2 years, 4 months agodangerelchulo
2 years, 8 months agoBoats
2 years, 8 months agoBoats
2 years, 8 months ago