

A penetration tester finds a PHP script used by a web application in an unprotected internal source code repository. After reviewing the code, the tester identifies the following: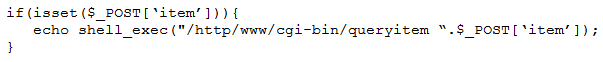
Which of the following tools will help the tester prepare an attack for this scenario?
BinarySoldier
Highly Voted 3 years, 5 months agostrawberryspring
3 years agostrawberryspring
Highly Voted 3 years agolifehacker0777
Most Recent 2 years agoDassler
2 years, 10 months agotahagoksoy
3 years, 1 month agotokhs
3 years, 4 months agorogal
3 years, 4 months ago