

DRAG DROP -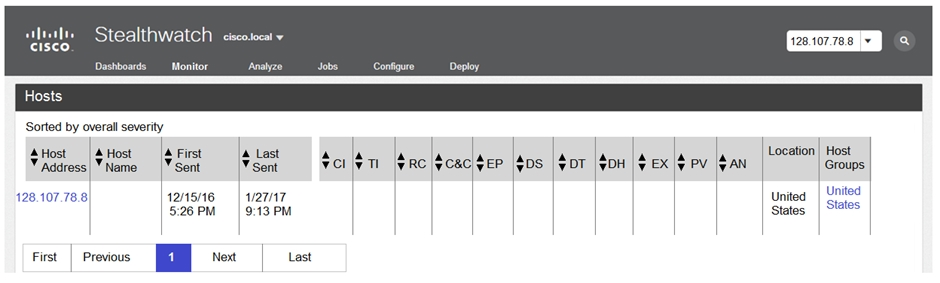
Refer to the exhibit. The Cisco Secure Network Analytics (Stealthwatch) console alerted with `New Malware Server Discovered` and the IOC indicates communication from an end-user desktop to a Zeus C&C Server. Drag and drop the actions that the analyst should take from the left into the order on the right to investigate and remediate this IOC.
Select and Place:
maxson69
Highly Voted 2 years agochongchangchi
1 year, 9 months agojay_c_an
Most Recent 9 months agojay_c_an
9 months agoDrVoIP
9 months, 4 weeks agoBobster02
2 years agoBobster02
2 years agojay_c_an
5 months ago