

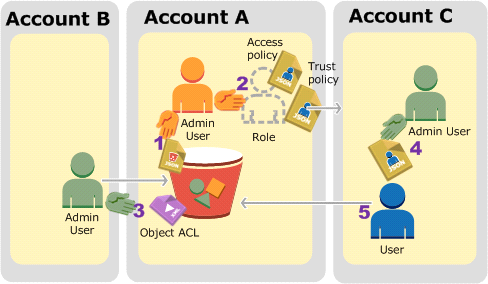
You are looking to migrate your Development (Dev) and Test environments to AWS. You have decided to use separate AWS accounts to host each environment.
You plan to link each accounts bill to a Master AWS account using Consolidated Billing. To make sure you keep within budget you would like to implement a way for administrators in the Master account to have access to stop, delete and/or terminate resources in both the Dev and Test accounts.
Identify which option will allow you to achieve this goal.

chauhr
2 months, 1 week agoamministrazione
8 months, 2 weeks agoMahesh430
1 year agoChristopher_AWS
1 year, 11 months agosedado77
2 years, 6 months agocldy
3 years, 4 months agojoe16
3 years, 5 months agoAkhil254
3 years, 6 months ago01037
3 years, 6 months ago01037
3 years, 6 months agocldy
3 years, 6 months agoExtHo
3 years, 7 months ago